
Introduction
Phishing has been both a popular and effective method used to steal personal and proprietary information from victims for over 25 years, with origins on the American Online (AOL) platform as early as 1995[1]. “AOHell” was a malicious piece of software that automated the collection of passwords and other data from victims on the online chat site.
Since then, phishing has evolved and several new approaches have emerged. While the method used is the malicious actors preference, they can range from generic to highly targeted. Mass-market phishing campaigns are cast to a wide group of potential victims in the hope that at least some will be tricked into sharing personal details. Spear phishing on the other hand is a technique that typically involves highly targeted campaigns towards a single or small group of victims. This approach is a favoured method of Advanced Persistent Threat (APT) groups, also referred to as Nation-State actors.
The COVID-19 pandemic saw a substantial increase in the use of smishing (phishing via SMS) and vishing (via voice) as methods to extort information from victims. Figures from the Anti-Phishing Working Groups (APWG)’s 2020 Q4 report detail that there were over 600,000 unique phishing websites tracked and almost 400,000 unique phishing email subject lines sent during this period[2].
Phishing in Ireland
In Ireland, we’ve seen a few recurring themes when it comes to the typical phishing emails, calls and SMS messages received. Some of the most common include:
- Packages that cannot be delivered due to customs owed.
- The Irish Revenue service issuing a tax rebate.
- The bank recording suspicious activity on your account.
- The Irish Government issuing energy subsidies.
- Amazon Prime renewals.
- Outstanding toll road charges.

At face value, these are all legitimate scenarios that one may encounter. However, the typical communication methods of the institutions mentioned above is not to send you a text message asking you to provide credit/debit card details to issue you a refund or ensure you card is not blocked.
Many online tools make it straightforward for malicious actors to spoof text messages claiming to be from your bank, delivery company or energy provider. Most implementations of SMS on mobile phones will group these malicious messages with legitimate messages – if the sender name matches. This makes it even more difficult to discern what is real or fake.
Example of a real phishing website
Quick disclaimer
The following steps/example were carried out in a controlled (sandboxed) environment and all details entered were fake. This is intended for demonstration/educational purposes only. If you suspect a link may be phishing, you should forgo even visiting the site in the first place, delete the message and move on with your day.
As they say on TV, don’t try this at home 🙂
Initial communication from the phisher
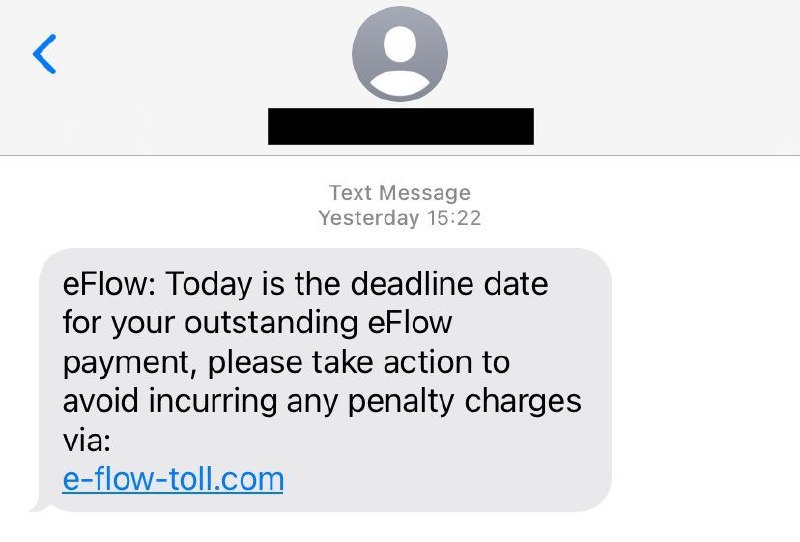
So what actually happens when an unsuspecting victim visits a malicious phishing website? To demonstrate this, we’ll use an example of a real phishing attempt I received via text message (smishing) recently. The phisher informed me that they were from eFlow (an Irish motorway tolling company) and that I had outstanding charges on my account. Spoiler alert: I didn’t. As you can see in Figure 2 below, the phisher wants me to visit e-flow-toll[.]com. For context, a quick Google ranks eflow.ie as the legitimate eFlow website – therefore we can assume this is suspect.
Sandbox detection & evasion techniques
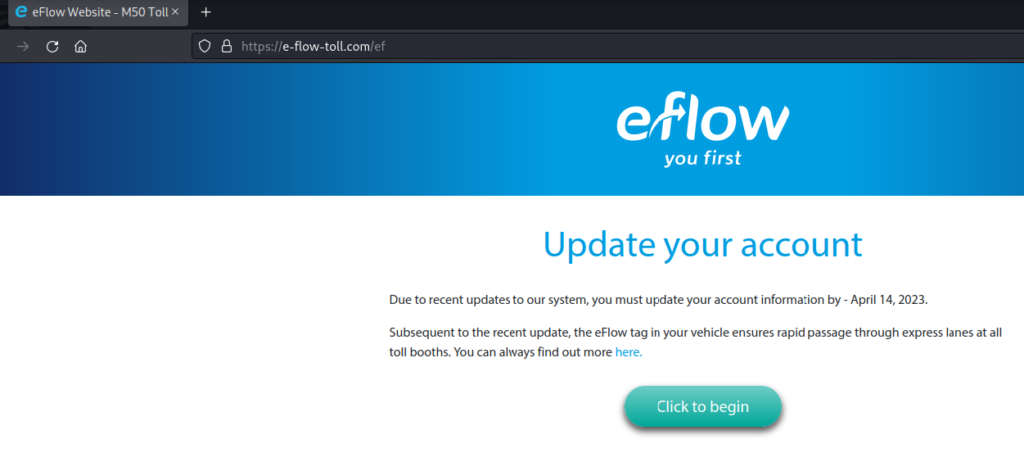
As you can see in Figure 2 above, the initial communication from the phisher was via text message. Therefore, it is most likely that the victim will browse to the website link on their mobile phone. Unfortunately, I forgot to take a screenshot of the mobile website before it was taken down but you’ll get the picture shortly. The website is available on my phone, but when I go to do some further investigation on my laptop I received a 404 – Not Found error for the same website. Seems strange, right?
This is a common technique used by phishers/malware developers called sandbox detection/evasion. Sandboxing is a practice used by security professionals to isolate malware/phishing websites in a controlled, secure, environment before running or browsing them to work out what they do. Naturally, the phisher would like to avoid security professionals or indeed automated software solutions flagging & subsequently blocking the website.
There are different techniques used to block sandboxes from executing malware or loading websites. Typically, a phishing website will make use of user agents to identify who or what the user is. In a legitimate use case, a user agent may be used to identify what type of device your browsing from and serve you the mobile site vs the desktop site. The examples below show a typical user agent for an iPhone 13 using the Safari browser and a Windows 10 PC using the Edge browser:
iPhone 13 User Agent:
Mozilla/5.0 (iPhone13,2; U; CPU iPhone OS 14_0 like Mac OS X) AppleWebKit/602.1.50 (KHTML, like Gecko) Version/10.0 Mobile/15E148 Safari/602.1
---------------------
Windows 10 User Agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.246In the case of e-flow-toll[.]com, the fact that it loads on my mobile browser but not on my desktop would suggest that there is likely some sandbox evasion techniques being used. However, we have technology on our side! We can use a browser extension to trick the phishing website into thinking we’re browsing from a mobile device. I won’t name the specific extension, that would make it too easy for them 🙂 – but it looks like that is the case, et voilà! We can now browse the site from the comfort of our desktop sandbox.
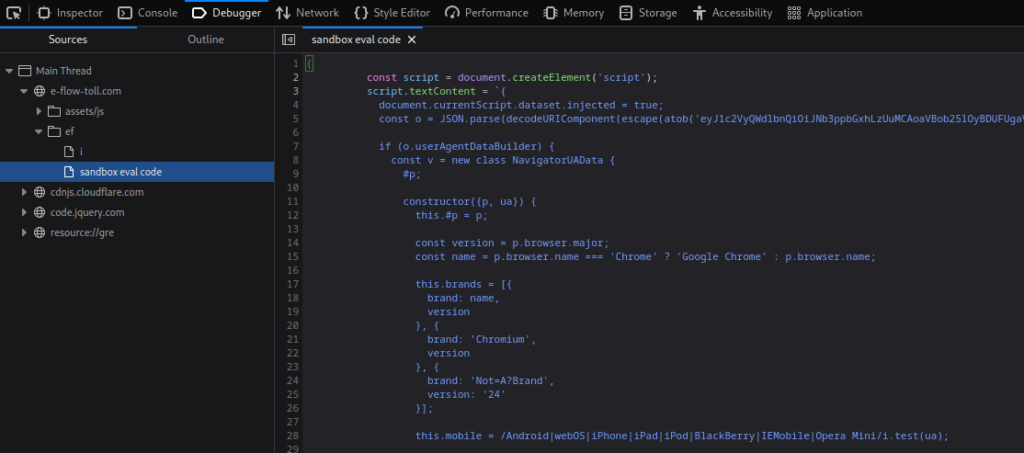
Now we’ve made it past the 404 – Not Found error, let’s check the websites source code and see if there are any signs that they were indeed trying to evade a sandbox. Using Inspect Element and viewing the Debugger, we can see the presence of some JavaScript code that is looking at the browsers user agent in an attempt to identify a sandbox. In this case, we don’t even need to look at the code – they’ve even named the file sandbox eval code!
Stealing your personal details
First and foremost, the phisher would like to steal some personal information, specifically: full name, home address, city and Eircode (Irish postcode). Later we’ll see attempts to capture credit/debit card and online banking details, but it is important to remember that this personal information is also useful to the phisher as they could use it to impersonate you in the future.
These websites can often look almost identical to the real deal. The wonders of modern technology make it easy to clone websites in an automated way, making easy for phishers to make changes under the hood and steal your details.
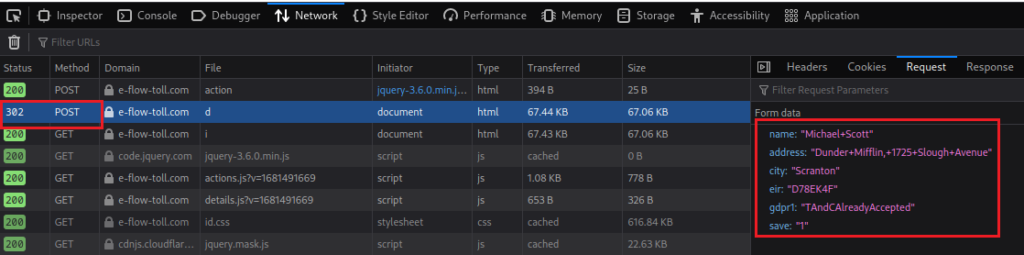
For kicks, let’s enter the details of everyone’s favourite office manager:
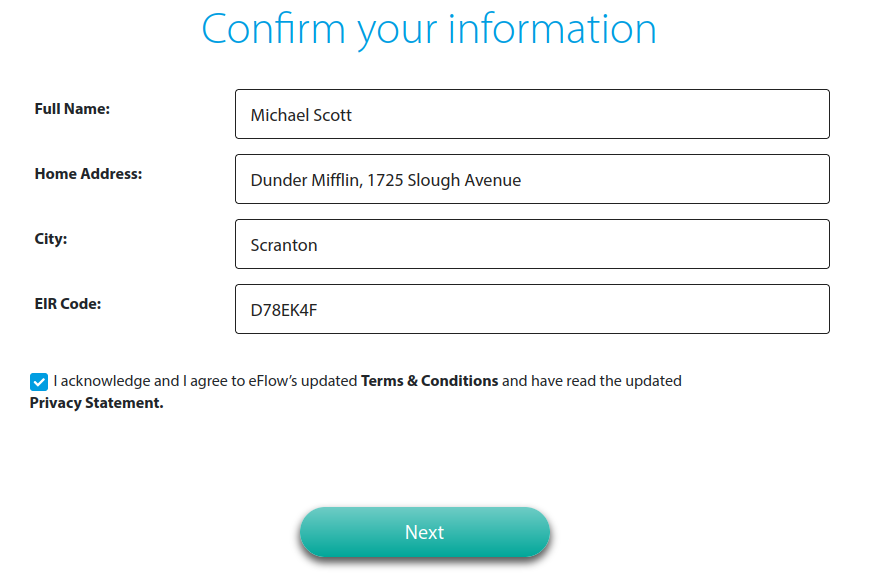
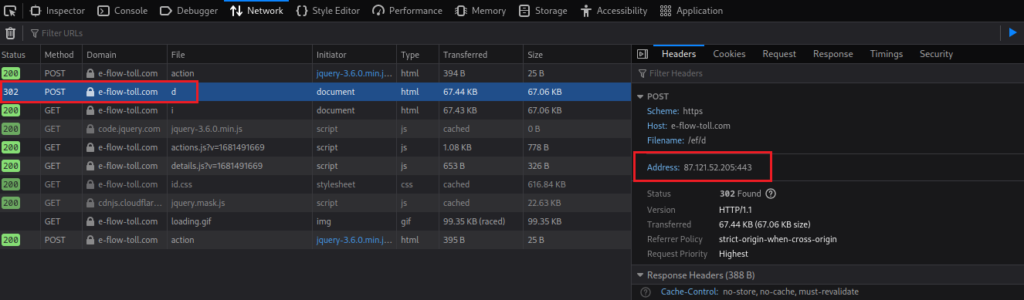
In ticking the checkbox we are confirming that we agree with how the phisher will handle our data in a GDPR compliant way, how considerate. Clicking Next will send these initial details to the backend server/database owned by the phisher, this is done via a HTTP POST request. In this case, the IP address of the server is 87[.]121[.]52[.]205. A quick search using an IP address lookup tool such as ipinfo.io tells us that this IP is hosted in Sofia, Bulgaria. While it is possible an Irish toll company could be hosting the site in Bulgaria, it is unlikely. In fact, a quick search of the actual eflow.ie domain shows that it is hosted in Ireland, as you would expect.
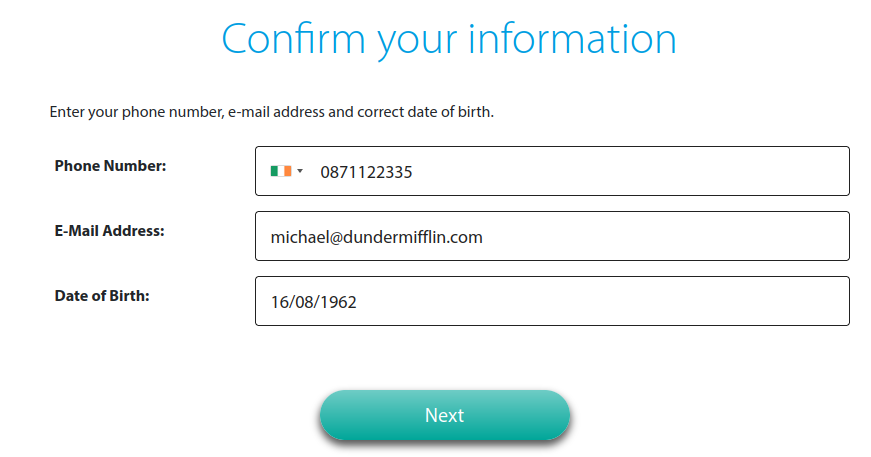
Next up – some more personal details, this time email, phone number and date of birth:
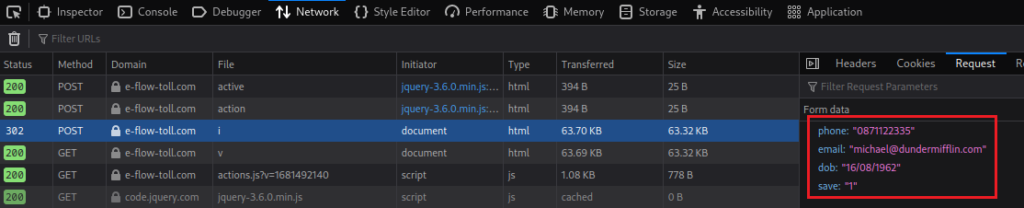
Again, the details are sent to the same Bulgarian IP address as seen in the network trace for this webpage:
Finally, to make it somewhat legitimate – your car registration details:
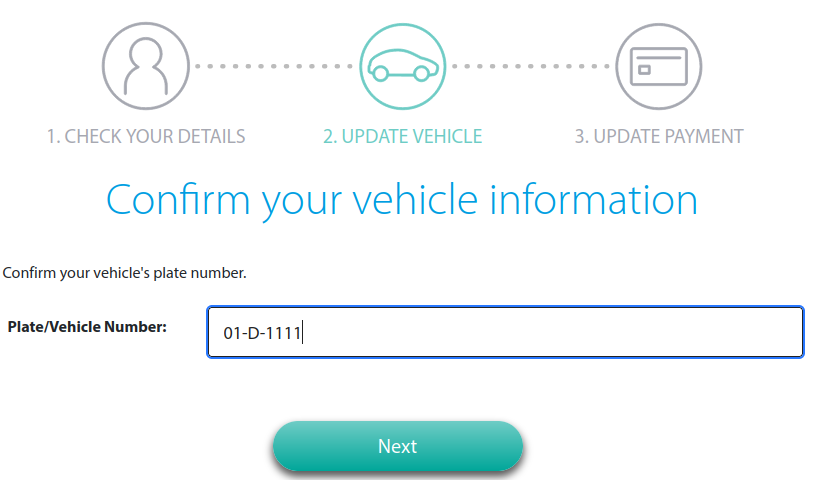
Stealing bank details
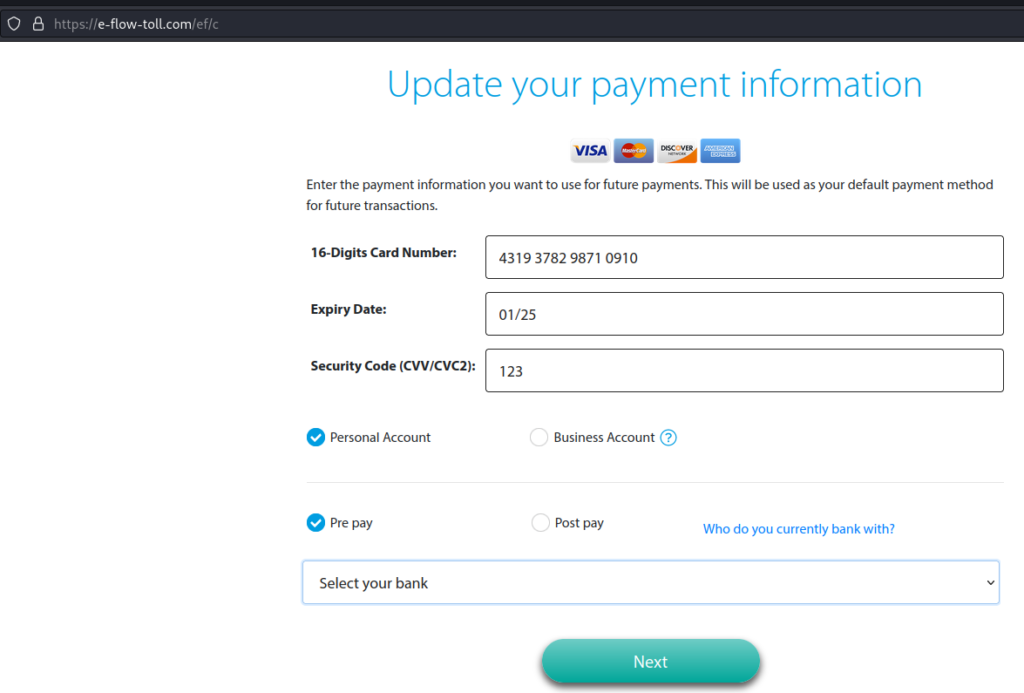
Next, the information the phisher is really after. While those initial personal details are useful for possible impersonation, what you’ve seen up to now is really a setup exercise or legitimisation of the website before requesting you to enter banking information.
Again, these are fake details for the purpose of this example.
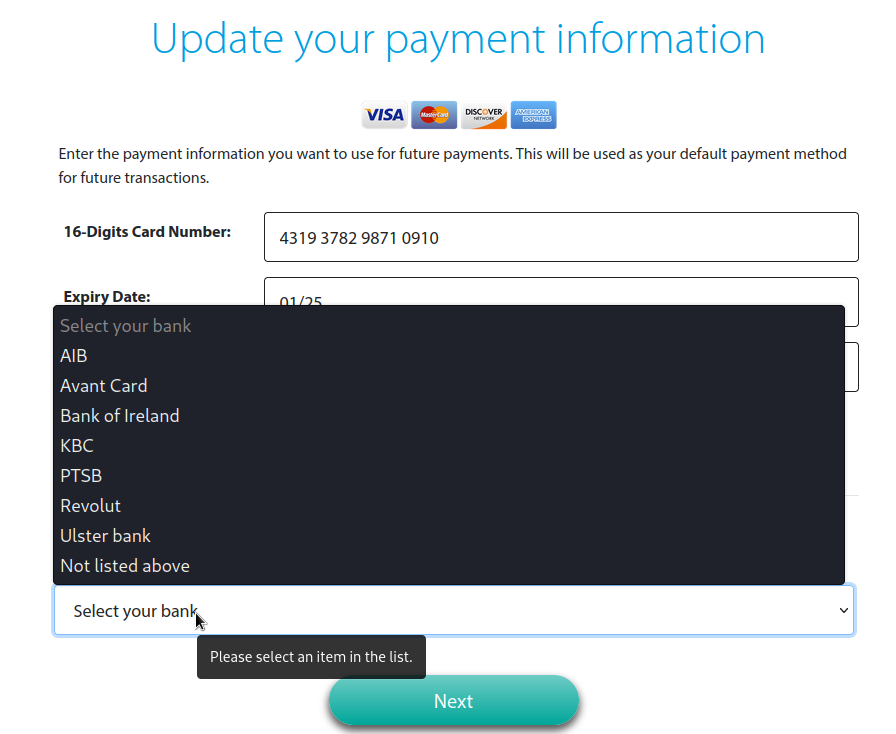
We’ve even been given a list of supported banks, what a great service!
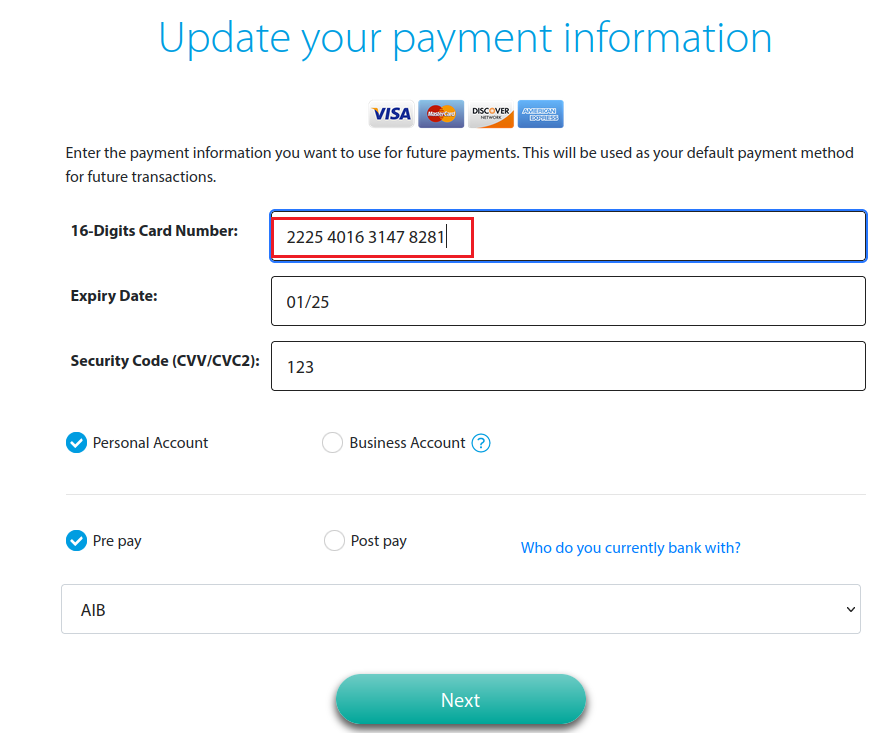
Validating ‘legitimate’ card details
At this point, when I clicked Next a red box appeared around the 16-digit card number field, suggesting the details entered were invalid. So there is some sort of form validation occurring, looking at this field in the HTML source code we can see a connection to a JavaScript file called splitter.js. So what does this file do? Well, as suspected – based on the variable names it is some sort of card validation. Again, as we saw with the sandbox evasion code – the phisher doesn’t leave much to the imagination here. A JavaScript comment is visible: ‘The Luhn Algorithm. It’s so pretty.’ can be seen.
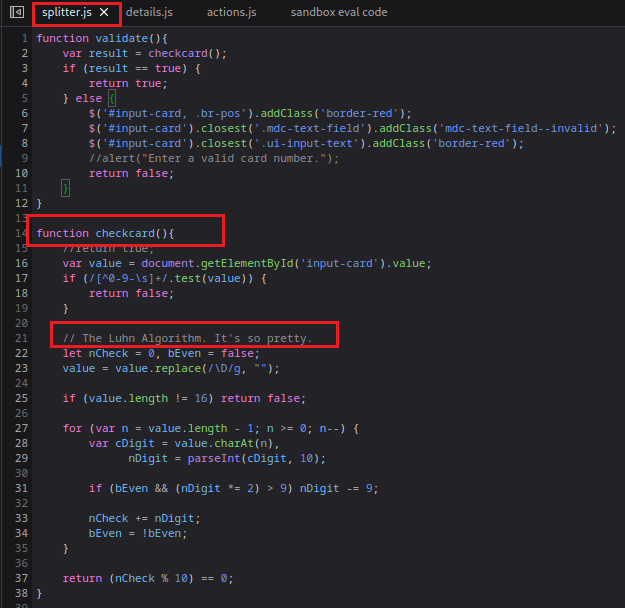
The Luhn Algorithm
So what exactly is the Luhn Algorithm? The algorithm also called the ‘Mod 10’ algorithm is used to validate a variety of identification numbers, including credit/debit cards, IMEI and national identification numbers for some countries[3]. In this case, the phisher is using it to verify that card details entered can be considered legitimate. I won’t cover how this algorithm works, but GoCardless have written a great article describing it here.
In order to pass this cardcheck() algorithm, we need to provide a card number that will satisfy it/the Luhn computation:
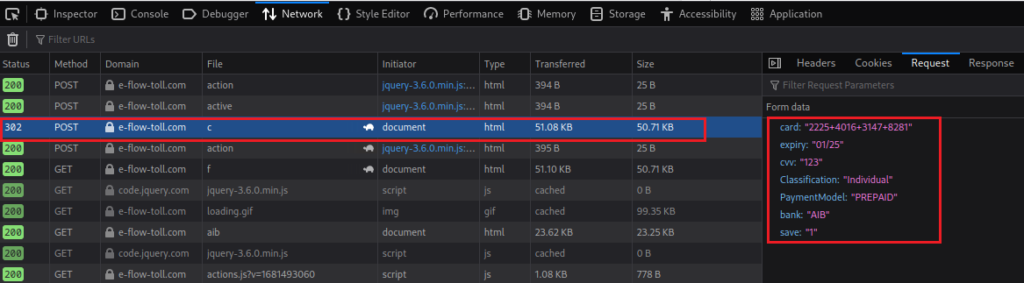
Reviewing the network trace for this activity, we can see our card details being shipped to the server hosted in Bulgaria and definitely not the tolling companies website hosted in Ireland:
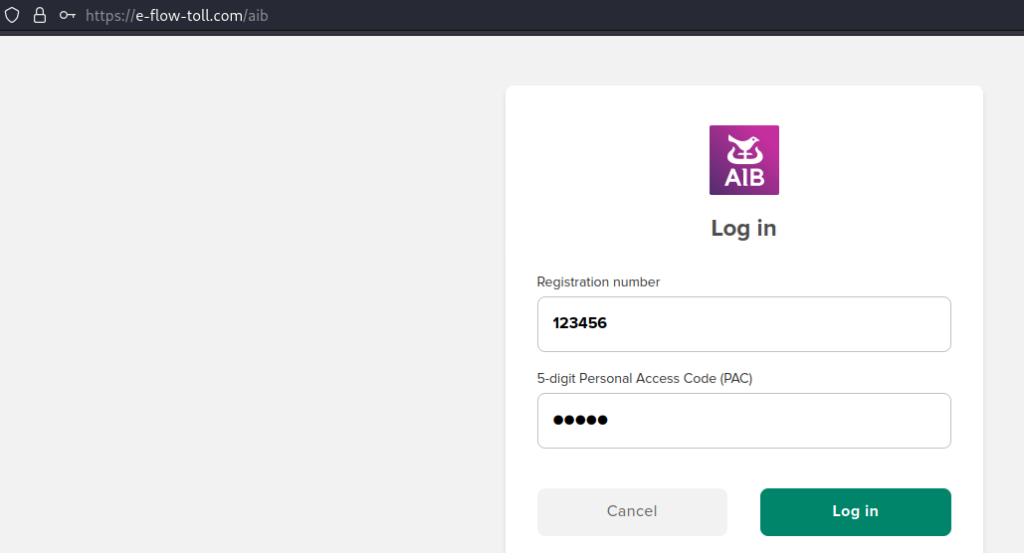
Stealing banking portal login details
Finally, a cherry for the top of the phisher’s cake – they’d like your banking login details, please:
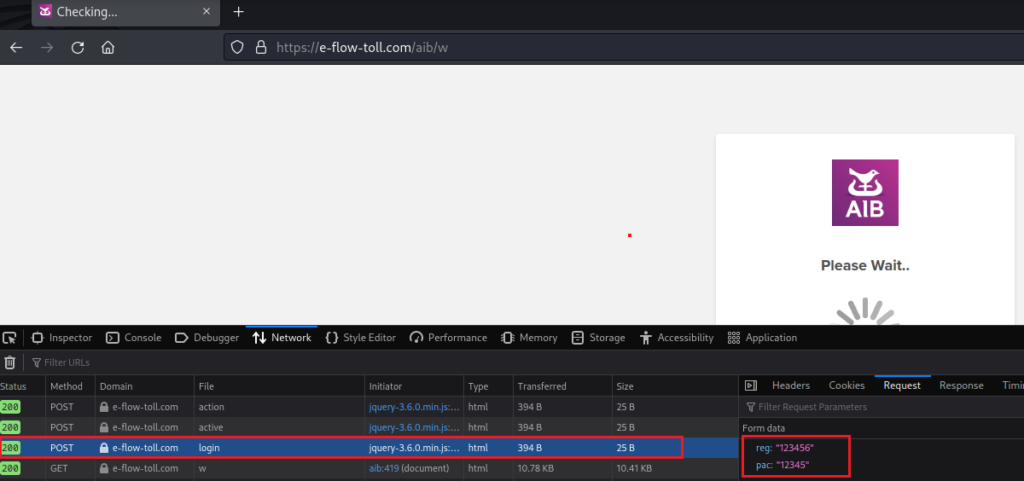
The final network trace shows the registration number and personal access code being shipped to Bulgaria too. At this point, the website goes into a ‘Please Wait..’ infinite spinning loop. This can either be a stalling technique or just a lazy way to closing out the loop of the phish:
Current state of play
At this point, I’ve provided personal details including name, full address, postcode, vehicle registration details, credit/debit card number and the name and login detail of my banking provider (albeit they are all fake). From here, the phisher could begin to process payments with my card details, use personal information to impersonate me and use my banking portal to transfer money or see my recent transactions. Not good!
Protecting yourself
So you’ve seen what happens under the hood when you enter your details into a phishing website, so how can you make sure you don’t become a victim? Phishers are continuously evolving their techniques and finding new ways to deceive us. As a result, we need to remain cognisant of these changes and not rest on our laurels.
As an example, in the past, looking for the green secure lock or certificate on the top of a website was part of many security awareness and training programmes. At that time, this was reasonable advice – there were cost barriers to obtaining these certificates that deterred phishers from using them. Now, as open-source certificate issuers exist – it is much easier for a phisher to automatically generate and install one into their phishing website. Thus, this can no longer be considered a mark of a “safe” website.
Critically analyse the communication
If you’ve received a text message from a seemingly legitimate organisation, such as the toll company seen in the example – take some time to critically analyse the message and context. As yourself some questions based on the message content, for example:
- Have I used the toll road recently?
If no, this already seems a bit suspicious. - How have the toll company contacted me in the past?
In Ireland, the toll companies typically communicate outstanding payments via the postal service. - Does this look like the real website for this company?
Take a moment to Google the company name, checking the top results. Google does a good job of ranking legitimate websites. - If you do browse to the website, consider what details the website is asking for?
Why would this website need my online banking portal details to process an outstanding toll payment?
General advice
- Trust your instincts, if you think something looks dodgy – it probably is. If you’re in doubt, ask someone for a second opinion. Again, critically analyse the content.
- If the SMS, email or phone call is claiming that you’ve won €1 million – it’s probably a little too good to be true.
- Don’t reuse passwords. If an attacker steals your password and your using the same one everywhere, they have access to everything. Consider using a password manager to generate and store unique passwords, most managers have an accompanying mobile app.
- Spread the word! If you’ve been sent a link you know is phishing, tell other people about it. ‘Have you heard of this latest one?’ these conversations subconsciously make people more aware of these types of scams.
Voice call
In the case of a voice call, again consider the context – has Amazon ever phoned you before about your Prime subscription expiring or custom charges? Typically these communications will be via email or in the Amazon website/apps. If in doubt, hang up and search for the customer service number on the website of the caller instead.
Enable two-factor authentication
Two-factor authentication (2FA) or multi-factor authentication is another tool you can use to protect yourself. This second factor of authentication is used in addition to your password or pincode when logging into a website or processing a payment. These can be in the form of a push notification or code sent via text message. This means that if a malicious actor steals your password, they’ll also need your second factor to login or process the payment. You should use 2FA wherever possible to protect yourself.
Virus Total
Virus Total is a website owned by Google that can scan websites and potentially malicious software to understand if it is indeed malicious. You can enter the link you received and see if there has been any malicious indicators associated with the website. Virus Total isn’t aware of every phishing website or malicious piece of software however, so it should be used as a guide and not gospel.
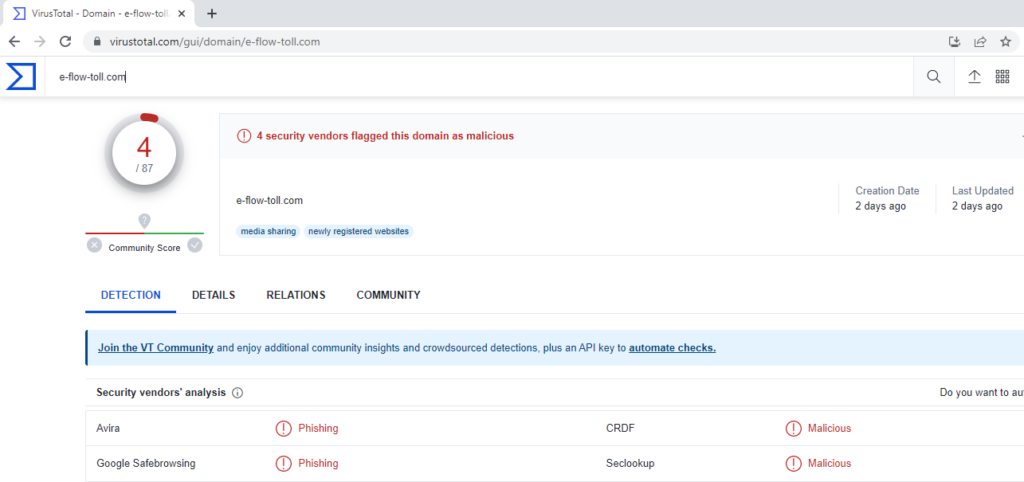
Google Safe Browsing
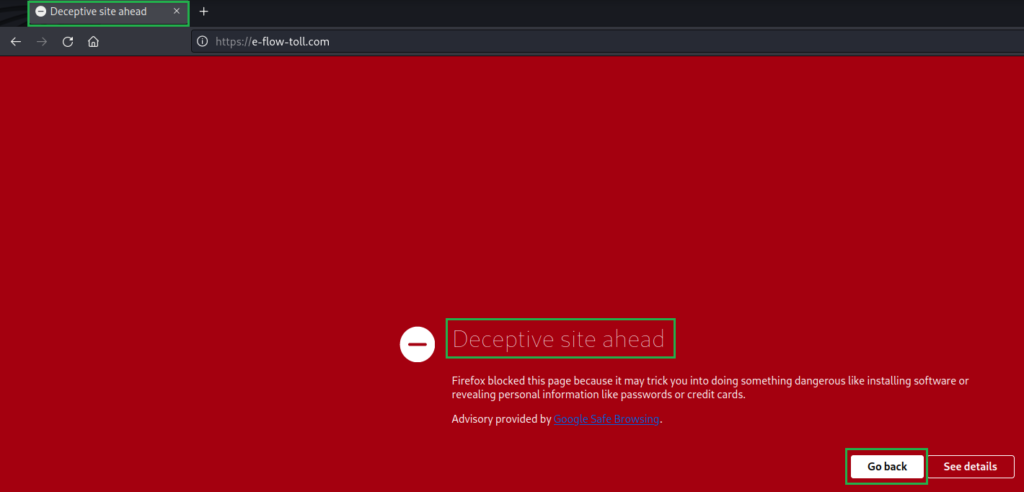
The Google Safe Browsing project was launched in 2005 to protect users from phishing websites. If the site has been flagged or reported, you may see the following page presented when you browse to the phishing site. Great! Google has already confirmed that this site is potentially malicious, we can close the webpage and delete the message from the phisher.
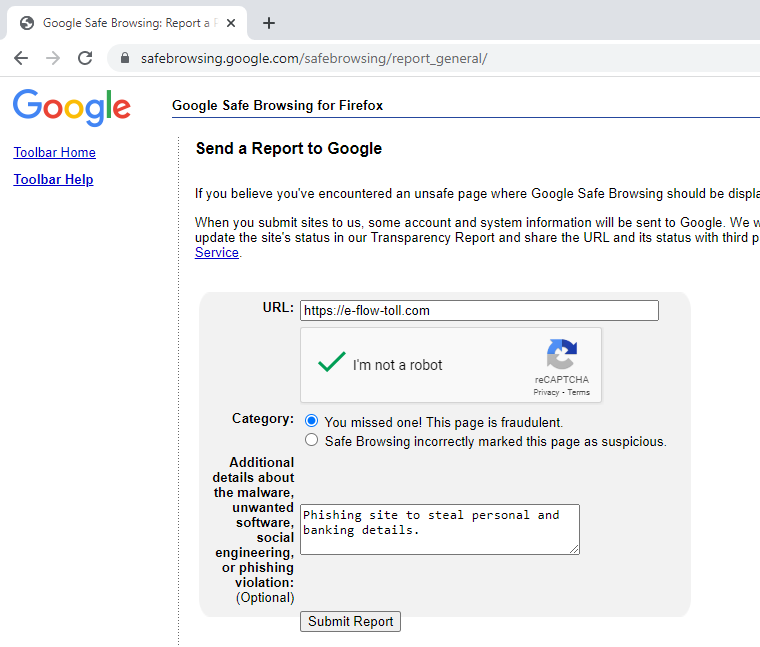
In the case that Google hasn’t flagged the site and you’re confident the site is indeed malicious, you can report the site yourself via Google’s Safe Browsing portal like so:
Conclusion
So where is our phishing website now? As of the time of writing, the site has been flagged by Google Safe Browsing as malicious and is no longer accessible – success! However, as mentioned standing up another website is simple for malicious actors, so it is important to remain vigilant.
Fin.
Thanks for taking the time to read this post, I hope you learnt something new. Anyone can fall victim to phishing campaigns, even security professionals have been successfully targeted in the past! If you know someone who could be particularly vulnerable to these types of scams, take the time to share some tips on staying safe with them.
If you have any feedback/corrections, please feel free to reach out to me via email below or on LinkedIn. I’d love to hear from you!
Stay safe out there!
-Dan